What Lexius users actually want
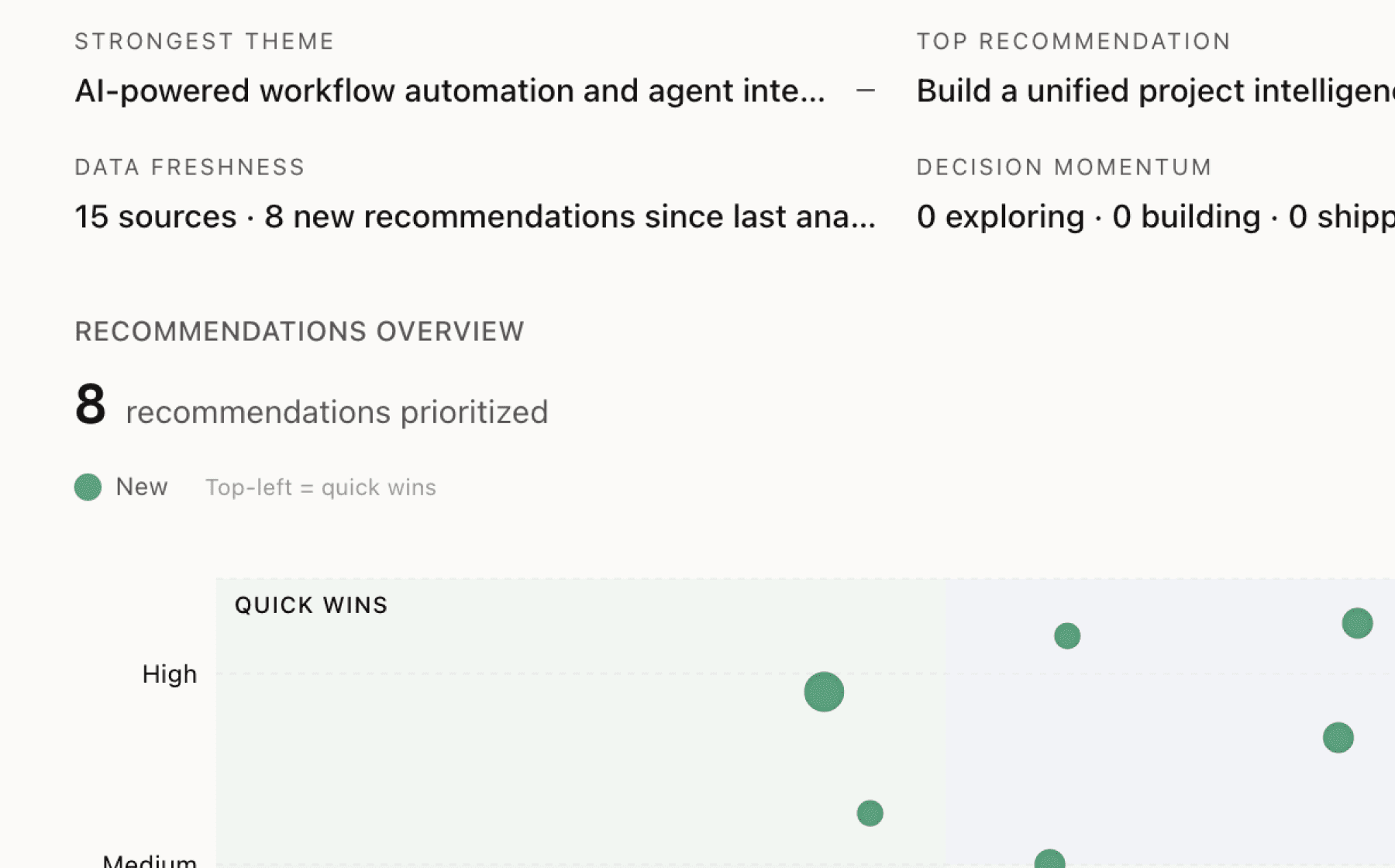
Mimir analyzed 13 public sources — app reviews, Reddit threads, forum posts — and surfaced 15 patterns with 8 actionable recommendations.
This is a preview. Mimir does this with your customer interviews, support tickets, and analytics in under 60 seconds.
Top recommendation
AI-generated, ranked by impact and evidence strength
Build an interactive ROI calculator that lets prospects model their specific store metrics and see projected payback timelines
High impact · Medium effort
Rationale
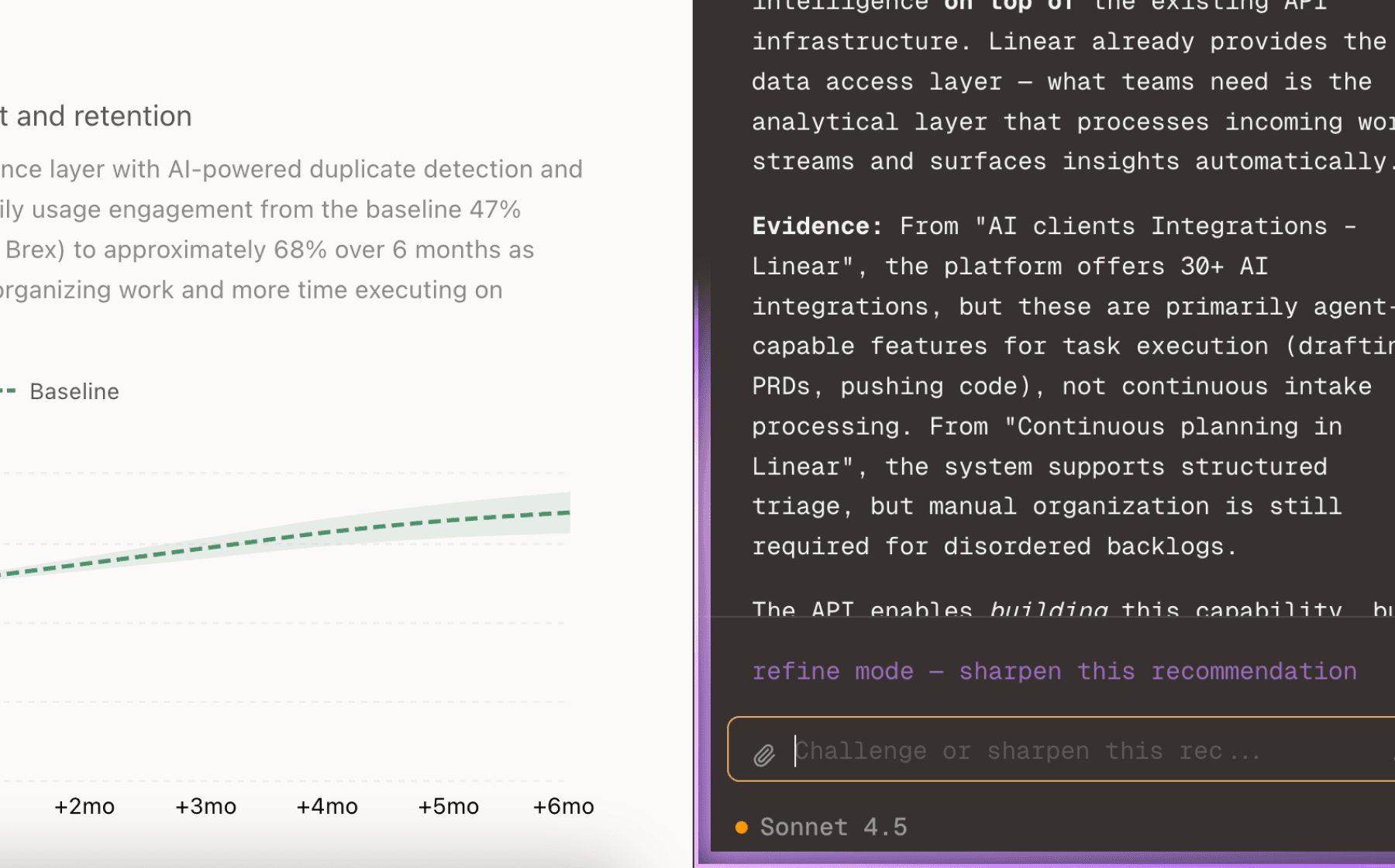
Users base adoption decisions on quantified financial impact—the data shows 9x ROI, 63% theft reduction, and system payback in days across multiple case studies. These concrete numbers drive engagement and retention because they validate the purchase decision. However, prospects need to translate these results to their own context before committing.
An ROI calculator that accepts inputs like current shrinkage rate, average theft incident value, and store size would generate personalized projections. This transforms generic case study metrics into actionable business justification that product managers and founders can present to stakeholders. The calculator becomes a retention tool by setting clear success benchmarks users will track post-implementation.
This addresses the critical need for documented financial proof while reducing friction in the sales process. Users who can model their own 30-day theft reduction and see projected savings are more likely to adopt and remain engaged as they validate those projections against actual results.
Projected impact
The full product behind this analysis
Mimir doesn't just analyze — it's a complete product management workflow from feedback to shipped feature.
Evidence-backed insights
Every insight traces back to real customer signals. No hunches, no guesses.
Chat with your data
Ask follow-up questions, refine recommendations, and capture business context through natural conversation.
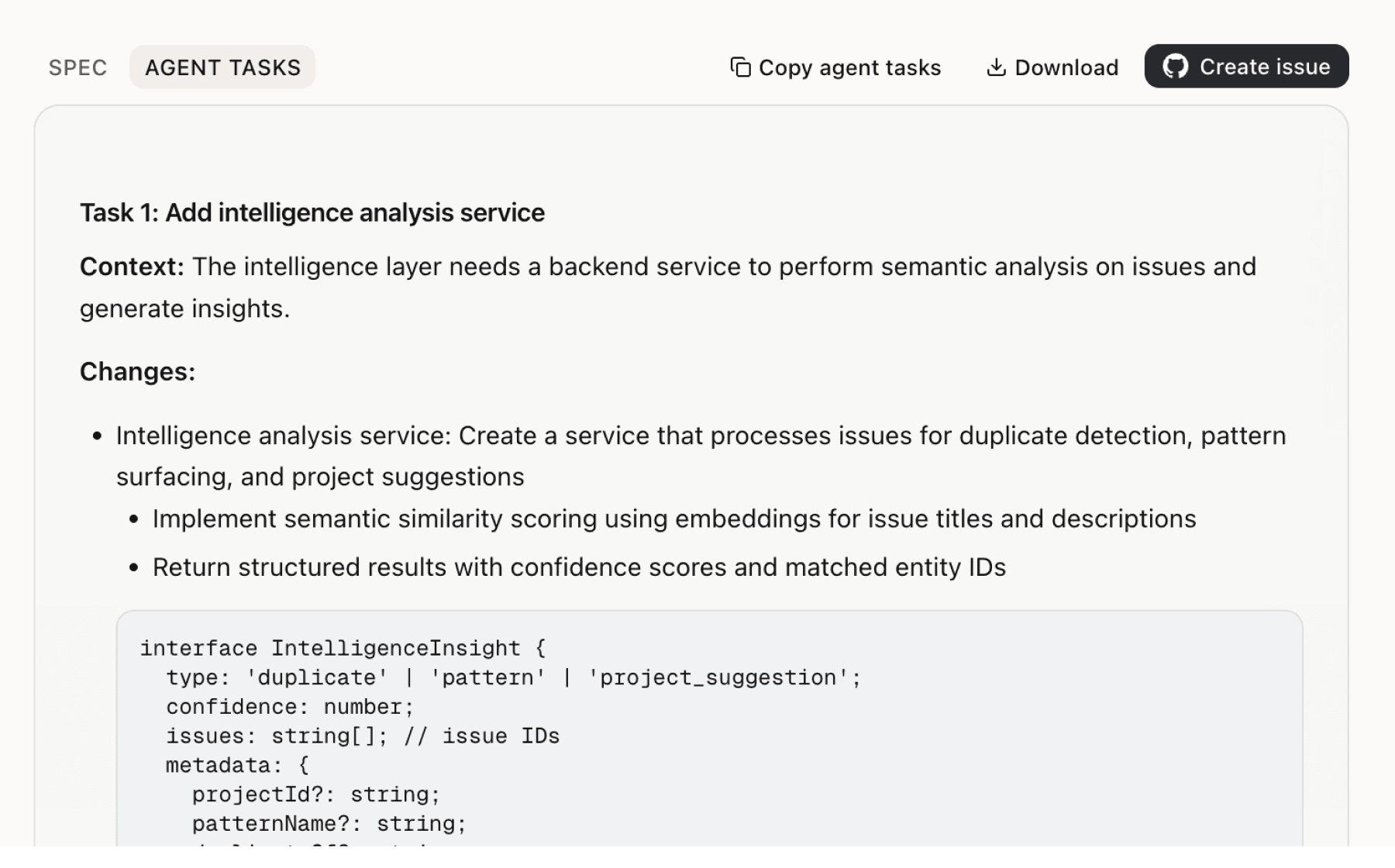
Specs your agents can ship
Go from insight to implementation spec to code-ready tasks in one click.
This analysis used public data only. Imagine what Mimir finds with your customer interviews and product analytics.
Try with your dataMore recommendations
7 additional recommendations generated from the same analysis
The evidence shows staff are addicted to the app and check it constantly, indicating the mobile alert system is the primary engagement driver. One case study reports 2-second detection time and immediate staff response, showing real-time alerts enable prevention rather than just documentation. However, current alert routing appears uniform rather than contextual.
The data shows AI models degrade over time due to drift and adversarial manipulation, requiring continuous monitoring of accuracy and precision metrics. Users need confidence that detection quality remains high as thieves adapt tactics and store conditions change. Currently there's no evidence users can verify system performance independently.
The evidence reveals diverse theft methods including two-bag tactics, tag swapping, fitting room lifts, and organized retail crime using sophisticated techniques. Current detection appears standardized rather than adaptive to each store's unique theft patterns. One case study explicitly notes the system caught tactics that would never be detected with traditional surveillance, suggesting value in continuous learning.
Multiple case studies report theft occurring in blind spots with inadequate camera coverage and users expressing relief at finally having eyes in previously unmonitored areas. However, the current plug-and-play installation doesn't appear to include systematic coverage assessment. Users may not realize they have gaps until theft occurs there.
Users justify initial adoption with concrete metrics like 63% theft reduction and 9x ROI, but there's no evidence they receive ongoing reporting to track these metrics post-deployment. The case studies show weekly theft savings and monthly prevention value, suggesting users need this data regularly to maintain confidence and justify continued investment. Without automated reporting, users must manually aggregate results or rely on memory of early wins.
The product emphasizes privacy-first design including no facial recognition, no data storage or selling, and minimal collection. However, the evidence shows users face regulatory requirements like GDPR compliance and need rigorous data governance. Large retailers and enterprises require detailed security documentation before adoption, yet there's no indication this exists in accessible form.
The product integrates seamlessly with existing camera systems, requiring no hardware upgrades and deploying in minutes. However, there's no evidence of integration with other retail systems where theft data creates value—POS for transaction correlation, inventory for shrinkage tracking, or incident reporting for loss prevention workflows. Users manage these systems separately rather than in a unified workflow.
Insights
Themes and patterns synthesized from customer feedback
Organizations require rigorous data governance, model protection against extraction attacks, compliance with privacy regulations like GDPR, and mitigation of AI bias. Retailers also face exposure to cyber threats including weak network security, outdated software, and inadequate encryption that must be addressed.
“Cybersecurity vulnerabilities in retail—weaknesses in network security, outdated software, and inadequate data encryption expose customer data to breaches.”
Users benefit from multi-layered deterrent strategies combining AI detection with environmental controls such as store layout optimization, lighting, signage, and blind spot elimination. This integrated approach to loss prevention improves overall effectiveness beyond detection alone.
“Strategic store layout with high-value items placed near front in well-lit areas, wide aisles, strategic mirrors, and elimination of blind spots”
While basic integration is straightforward, broader implementation requires employee training, vulnerability assessments, and coordination across technology stacks including CCTV, POS analytics, RFID, and SIEM systems. Implementation costs and specialized expertise requirements can create barriers for some retailers.
“Modern POS systems integrated with inventory management, weight checks at checkout, and RFID tags for real-time merchandise tracking and shrinkage reduction”
Organizations need real-time inventory accuracy systems with regular cycle counts and data analysis of shrinkage patterns to identify discrepancies early. Timing analysis and continuous performance monitoring enable retailers to track loss prevention effectiveness and measure impact.
“Regular inventory cycle counts and physical audits with inventory management software to maintain accurate records and identify discrepancies”
Retailers need comprehensive training programs covering shoplifting behavior recognition, proper incident handling protocols, and discreet reporting mechanisms to operationalize AI detection across teams. Effective staff training ensures the system translates detection into action.
“Staff training to recognize shoplifting signs including suspicious browsing, item concealment, nervous behavior, and proper protocols for handling incidents”
AI detection systems require ongoing monitoring due to data drift and adversarial manipulation that degrades accuracy over time. Continuous monitoring of model performance metrics and drift detection algorithms are essential to maintain system effectiveness and user confidence in detection quality.
“AI-powered systems improve over time through machine learning, becoming more accurate with every incident”
Users face multiple theft types including shoplifting, organized retail crime, employee theft, refund fraud, and tag swapping, with thieves employing increasingly advanced tactics like two-bag techniques and coordinated group operations. Detection systems must identify specific suspicious behaviors across different scenarios and evolve to catch sophisticated methods early.
“Product detects specific theft behaviors: item concealment in jacket, personal bag, and back-of-store activities”
Users spend excessive time manually reviewing footage and monitoring loss prevention, consuming resources that could focus on customer service. AI automation frees staff to handle higher-value activities while maintaining continuous surveillance, directly improving store operations and daily engagement with the system.
“Hours spent manually reviewing footage to identify incidents”
Lexius requires no new hardware installation, integrates with multiple camera types, and deploys in minutes with minimal setup friction. This plug-and-play capability into current systems reduces adoption barriers and accelerates time-to-value for retailers with established surveillance.
“Lexius is a plug-and-play AI crime detection system that integrates with existing camera infrastructure without requiring new hardware installation.”
Shoplifting creates cascading costs including inventory disruption, rising consumer prices, operational expenses, reputation damage, insurance claims, and staff morale impact. Global retail theft exceeds $70 billion annually, with inflation driving increased incidents, making loss prevention a pressing business priority.
“Shoplifting burdens grocery stores of all sizes, leading to rising costs, stock disruptions, and thinner margins”
Users prioritize solutions that protect customer privacy and don't disrupt the shopping experience, making non-intrusive security a key differentiator. The product's approach—no facial recognition, no data storage/selling, and minimal data collection—builds trust with retailers and customers.
“Product emphasizes privacy-first design: does not analyze skin color/race, does not access store footage, and does not store/sell customer data.”
Store owners are often unaware of the actual scale of theft until implementing AI detection, which reveals patterns and tactics that traditional surveillance cannot catch. This discovery of previously undetected incidents provides critical business intelligence that drives engagement and justifies continued use.
“Store owner was unaware of true magnitude of theft problem until Lexius visualization”
Users prioritize concrete metrics—63% shoplifting reduction within 30 days, 90% reduction in footage review time, and clear return on investment—to justify adoption and measure success. Documented case studies demonstrating rapid payback directly drive user engagement and retention.
“Shoplifting reduced by 63% within 30 days of installation”
Users need instant automated detection of suspicious behavior with rapid alerts sent to staff mobile devices, enabling discreet intervention before theft occurs. This core capability directly addresses the failure of traditional surveillance to prevent loss, and high app engagement indicates strong daily reliance on this feature.
“Stop shoplifters before they walk out. Lexius is AI security that alerts your staff in real-time, no new cameras needed.”
Traditional camera systems fail to detect theft in overlooked areas and lack proper detection at entry/exit points and high-value zones. Users need comprehensive coverage that identifies suspicious behavior across all previously unmonitored blind spots, which is essential for effective loss prevention.
“Theft often occurred in blind spots where camera coverage was inadequate”
Run this analysis on your own data
Upload feedback, interviews, or metrics. Get results like these in under 60 seconds.