What Cyberdesk users actually want
Mimir analyzed 5 public sources — app reviews, Reddit threads, forum posts — and surfaced 13 patterns with 5 actionable recommendations.
This is a preview. Mimir does this with your customer interviews, support tickets, and analytics in under 60 seconds.
Top recommendation
AI-generated, ranked by impact and evidence strength
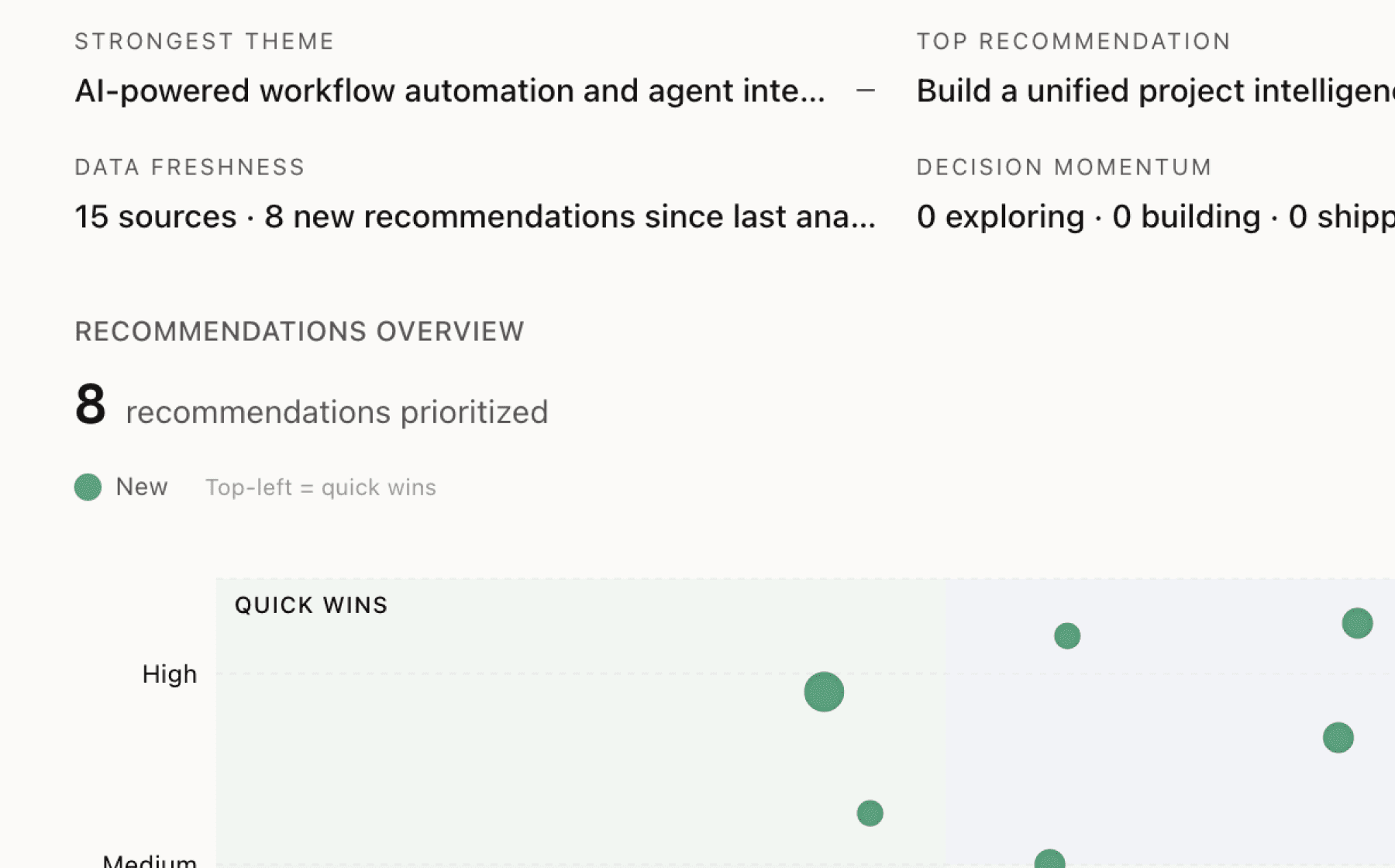
Publish a dedicated enterprise security and compliance guide
High impact · Small effort
Rationale
Four sources highlight a fundamental gap between the product's access to sensitive customer environments and contractual security guarantees. Enterprise buyers need concrete evidence of how Cyberdesk protects their data, not disclaimers about what the company cannot guarantee. Product managers evaluating Cyberdesk face procurement gatekeepers who require documented security controls, data handling procedures, and incident response protocols.
While HIPAA and SOC 2 Type 2 certifications provide baseline credibility, they don't answer specific questions about data residency, encryption standards, third-party subprocessor management, or backup procedures. The current privacy policy mentions third-party data sharing and international transfers but provides no operational detail.
A comprehensive security guide should document encryption at rest and in transit, data retention policies, subprocessor lists with geographic locations, backup and disaster recovery procedures, and audit log availability. This single artifact transforms security from a procurement obstacle into a competitive differentiator and directly addresses the friction identified across multiple themes.
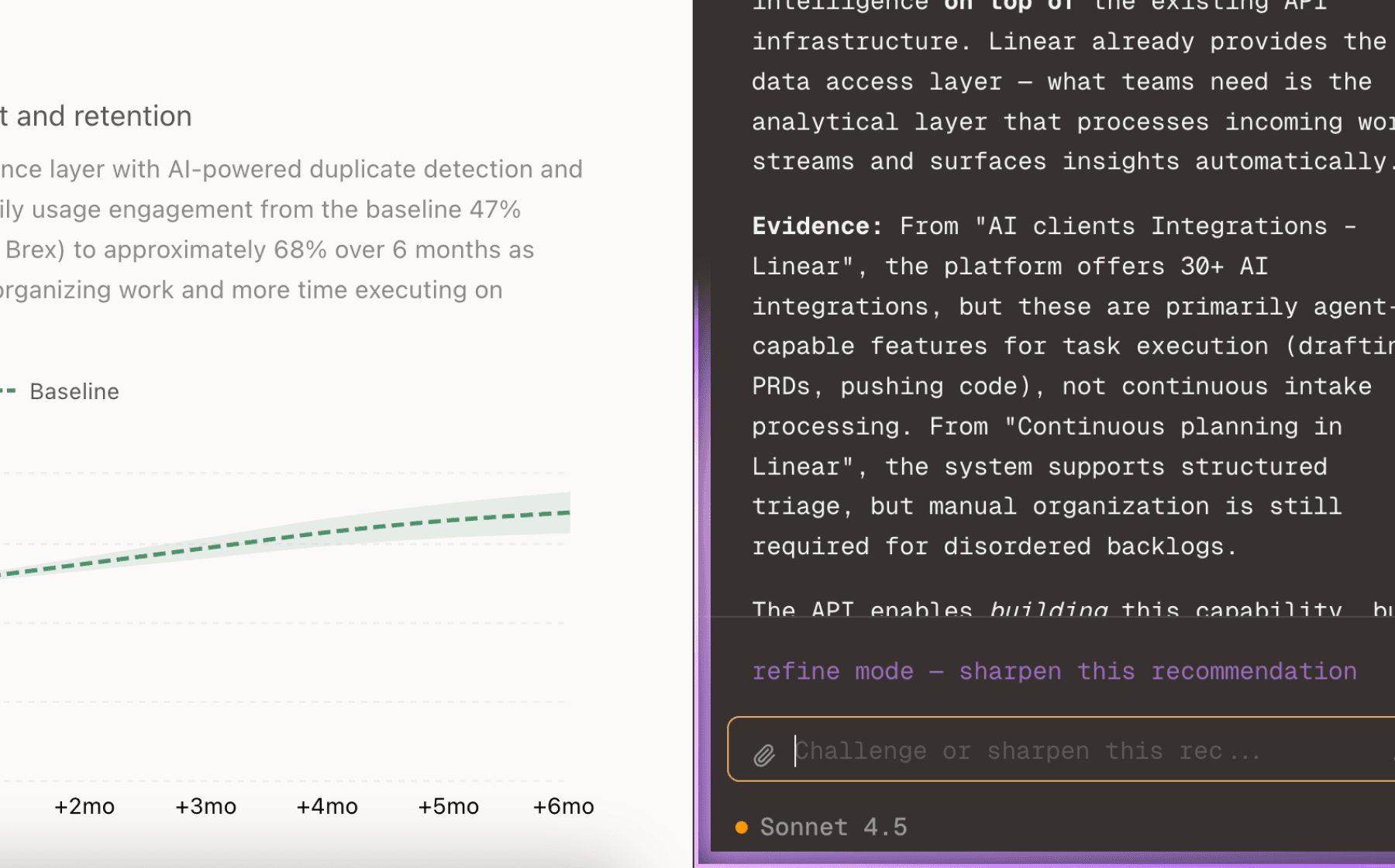
Projected impact
The full product behind this analysis
Mimir doesn't just analyze — it's a complete product management workflow from feedback to shipped feature.
Evidence-backed insights
Every insight traces back to real customer signals. No hunches, no guesses.
Chat with your data
Ask follow-up questions, refine recommendations, and capture business context through natural conversation.
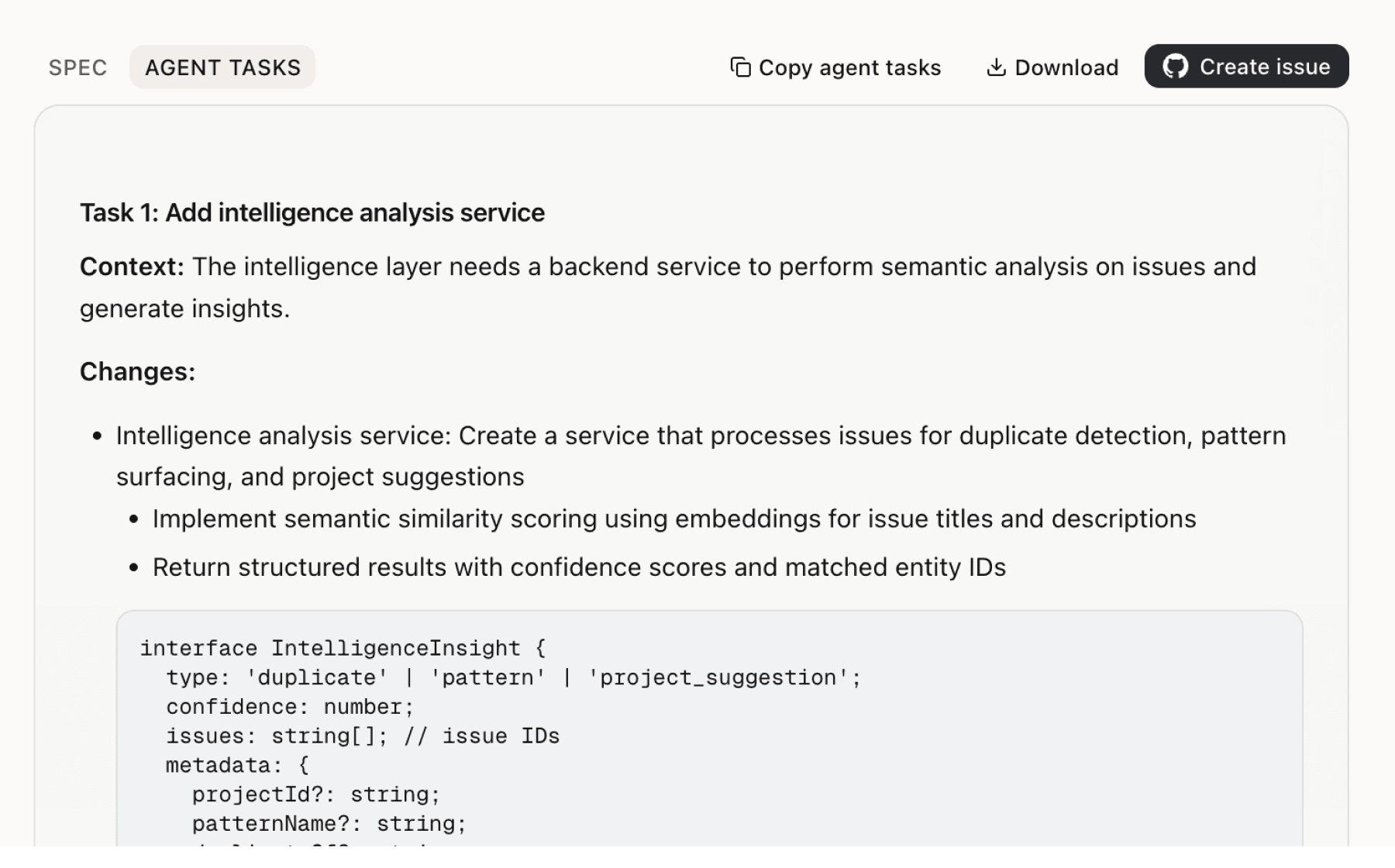
Specs your agents can ship
Go from insight to implementation spec to code-ready tasks in one click.
This analysis used public data only. Imagine what Mimir finds with your customer interviews and product analytics.
Try with your dataMore recommendations
4 additional recommendations generated from the same analysis
Enterprise buyers managing production automation workflows need predictability. The current terms allow Cyberdesk to suspend or terminate access at any time for any reason, which directly conflicts with how product managers and engineering leads evaluate vendor risk. No team will route critical healthcare patient workflows or financial transactions through a service that can disappear without notice.
The core value proposition is automating legacy Windows applications through plain English descriptions, but new users still face a blank canvas problem. Product managers evaluating Cyberdesk need to see concrete examples of what workflows look like for Epic, SAP, Cerner, or other enterprise applications common in healthcare, finance, and logistics.
Product managers and engineering leads evaluating Cyberdesk face an adoption gap: the product's minimal infrastructure requirements reduce deployment friction, but users still need to install software and connect to their environments before experiencing the core value proposition. This creates a commitment barrier before users understand what they're committing to.
The privacy policy states that user data may be transferred to and processed in the United States, where data protection laws may differ from the user's jurisdiction. For healthcare organizations subject to HIPAA or international companies with GDPR obligations, this creates a specific procurement obstacle. Engineering leads need to know where their automation data will be stored and processed before they can complete vendor risk assessments.
Insights
Themes and patterns synthesized from customer feedback
The product requires no firewall rules, VPNs, or proxies and works on both physical and virtual Windows machines, lowering the barrier to deployment. This ease of installation is a competitive advantage for product teams with limited infrastructure flexibility.
“Product emphasizes ease of installation: driver works on physical/virtual Windows machines with no firewall rules or VPN required”
Cyberdesk collects login times, features used, and platform interactions to analyze usage patterns and enhance user experience. This data collection enables the company to understand engagement metrics and identify retention risks, though it requires transparency to maintain user trust.
“Cyberdesk collects usage data including login times, features used, and platform interactions to analyze usage patterns and enhance user experience.”
Cyberdesk's foundation in AI computer use models (agents that interact with interfaces like humans) rather than traditional RPA/PyAutoGUI is a technical differentiator that addresses reliability concerns. This architectural choice supports the product's value proposition of reducing debugging and maintenance burden.
“Differentiator: built on computer use models (AI models that use computers like humans) vs. traditional RPA/PyAutoGUI”
Smart caching with fallbacks makes repeated desktop tasks faster, cheaper, and more deterministic—addressing cost sensitivity and reliability concerns for product managers managing automation budgets. This feature improves retention by reducing per-execution costs over time.
“Intelligent caching feature makes repeated desktop tasks cheaper, faster, and deterministic with smart fallbacks”
The signup and login flows offer both Google OAuth and email/password authentication with minimal required fields (first name, last name, email, password), supporting frictionless onboarding for new users.
“Sign-up form requires basic information: first name, last name, email, and password to create account”
Cyberdesk's Y Combinator backing provides institutional credibility and validation that may reassure product managers and engineering leads evaluating an early-stage vendor. This reduces perceived adoption risk.
“Backed by Y Combinator, signaling credibility and institutional support”
Support for both Windows and MacOS expands the product's applicability beyond Windows-only shops, though the current market focus appears to be Windows-centric. This provides flexibility for multi-platform development teams.
“Cross-platform support: driver works on both Windows and MacOS”
Product managers and engineering leads expect built-in observability dashboards, comprehensive APIs (TypeScript/Python), and automation features (scheduling, retries, error handling). These are table-stakes for enterprise adoption and directly impact user engagement by enabling visibility into agent performance.
“Built-in observability dashboard for managing workflows, viewing run logs, and managing machines”
Cyberdesk's HIPAA and SOC 2 Type 2 certifications (monitored by Delve) are explicit enterprise requirements that remove procurement obstacles for healthcare, finance, and logistics organizations. This is a key differentiator in the target market.
“Enterprise compliance: HIPAA and SOC 2 Type 2 certified, monitored by Delve”
Cyberdesk shares user information with third-party service providers for payment processing, data analysis, and customer service, expanding the security attack surface. Combined with international data transfers to the US, this increases complexity for enterprises with data residency or privacy requirements.
“Cyberdesk may share user information with third-party service providers for payment processing, data analysis, and customer service.”
Cyberdesk reserves the right to suspend or terminate access at any time for any reason, which creates uncertainty for enterprise buyers managing critical automation workflows. This open-ended termination clause may deter adoption by product managers and engineering leads managing production systems.
“Company reserves right to suspend or terminate access at any time for any reason”
Developers need to automate legacy Windows applications lacking APIs, and Cyberdesk's core value proposition is enabling workflow creation through natural language descriptions rather than traditional scripting. This directly reduces friction for the target user—product managers and engineering leads can deploy automations by explaining tasks in plain English.
“Plain English workflow creation: users can write automations by explaining tasks in natural language like 'Open Epic, add a patient...'”
Cyberdesk collects sensitive virtual desktop content (files, applications, AI configurations) but provides limited security guarantees, placing data protection responsibility on users. This gap between the product's access to sensitive customer environments and the company's contractual liability limitations creates friction for product managers and engineering leads evaluating enterprise adoption.
“Virtual desktop content (files, applications, AI agent configurations) generated or stored within user environments is collected and processed by Cyberdesk.”
Run this analysis on your own data
Upload feedback, interviews, or metrics. Get results like these in under 60 seconds.